CybAfriqué is a space for news and analysis on cyber, data, and information security on the African continent.
HIGHLIGHTS
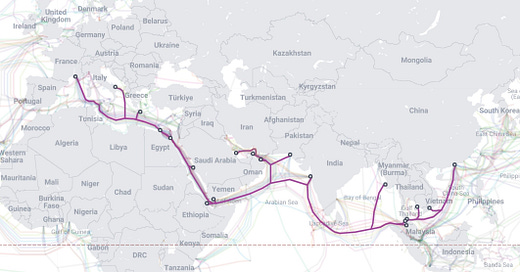
How to build resilient subsea cables
A coalition of four subsea cable operators across the globe— PCCW, Sparkle, Telecom Egypt, and Zain Omantel, signed a Memorandum of Understanding (MoU) to build AAE-2, the successor to one of the world’s most critical subsea cables, Asia–Africa–Europe-1 (AAE1). To understand why this is interesting, we need to revisit how subsea cables function.
The basics, which you might have heard several times, is that subsea cables are the backbones of the internet, they are resource-intensive, and in recent times, they’ve been subjected to cuts, causing devastating internet chokedowns, especially in vulnerable regions like Africa and Asia where there’s no robust cable networks to seamlessly pick up compromised traffic. You can read about cable shortages in our past edition.
ICYMI: Africa’s cable problem
The biggest problem with this physical infrastructure is that it breaks. And it breaks most often in predictable, high-traffic areas. The Red Sea is a popular example. It connects Asia, Africa, and Europe through the shortest, most direct maritime route, making it prime real estate for subsea cables. However, it is also a hub of heavy shipping traffic, which makes it a strategic vulnerability for both malicious actors and people just making mistakes. In February 2024, for instance, three separate cables in the Red Sea, serving major providers like Seacom, TGN, and AAE-1 (the predecessor to AAE-2), were severed amid attacks from Houthi rebels, allegedly by a ship's anchor. This single incident caused one of the most disruptive internet chokedowns across Africa and Asia (and not Europe because there were more cables to pick up the traffic).
Geographic chokepoints like the Red Sea create a dangerous concentration of risk. An estimated 17% of the world's internet traffic is funneled through cables in the Red Sea, putting a massive portion of global connectivity at the mercy of a stray anchor or a minor geological event in one narrow, shallow sea.
It also creates a business and political bottleneck. To get data through this critical corridor, companies must traverse Egypt. This means paying fees to the state-owned Telecom Egypt, giving a single entity significant leverage over global data flows. For businesses and nations, this single point of reliance is both a risk and a cost.

Unlike ships, subsea cables cannot actively protect themselves against threat actors like pirates and military actors.
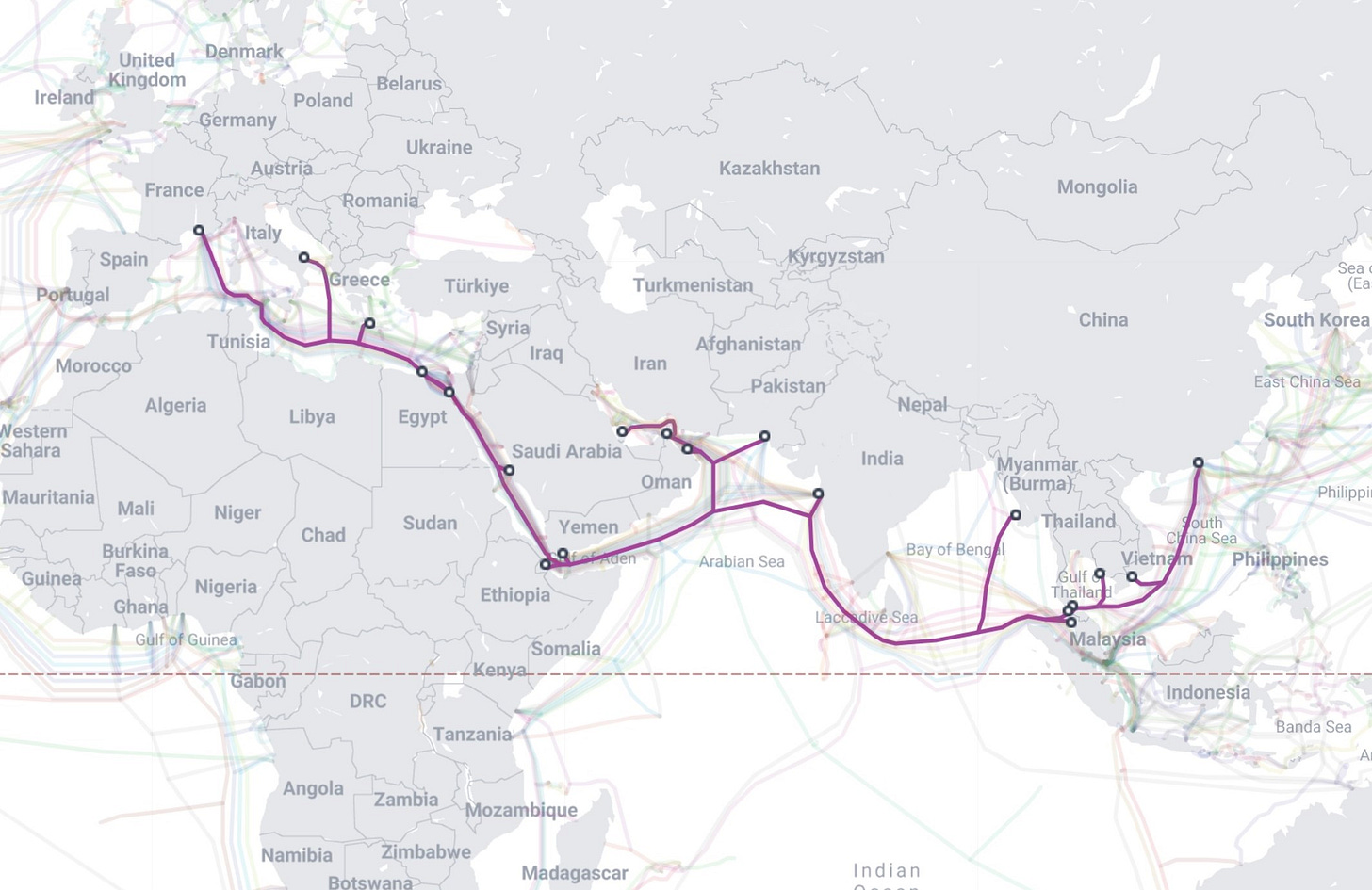
Turns out the best way to make a subsea cable resilient is to put it on land, and that’s what the architects of AAE-2 are doing. Large sections of AEE-2 are expected to pass on land, instead of running entirely underwater.
Instead of running entirely underwater through the most congested parts of the Red Sea, AAE-2 will come ashore in the Arabian Peninsula. It will then travel over a secure, terrestrial (overland) fiber network before re-entering the sea. It will also leverage Telecom Egypt's robust terrestrial infrastructure to cross from the Red Sea to the Mediterranean, avoiding chokepoints in the Suez Canal region.
This model is enabled by the very nature of the consortium, which includes global partners with extensive and secure overland networks. While other regions have used terrestrial fibre to bypass smaller problem areas, AAE-2 is one of the most ambitious examples of using this hybrid strategy to enhance the resilience of an entire intercontinental route.
Another interesting feature of AAE-2 is its design for "cross-connection." This means the cable won't be a closed-off superhighway. Instead, at its landing stations, it will be built to easily connect with dozens of other subsea and terrestrial cable systems. Major interconnection hubs for data, like Marseille, France, and Singapore, operate on the same principle. In Marseille, over 15 subsea cables land and interconnect, creating a vibrant, competitive, and resilient ecosystem where data can be rerouted efficiently.
AAE-2 aims to bolster this model, particularly at its landing points in the Middle East and Egypt, turning them into even more powerful data hubs. This means traffic from AAE-2 can be easily switched to another cable heading to the Americas or even cables traversing the same route as AAE-2, making it easier to reroute traffic from either side during cuts.
AAE-1 was the world’s longest subsea cable for over fifteen years, until Meta-backed Alcatel’s 2Africa, a subsea cable circumventing the entirety of Africa, took that position.
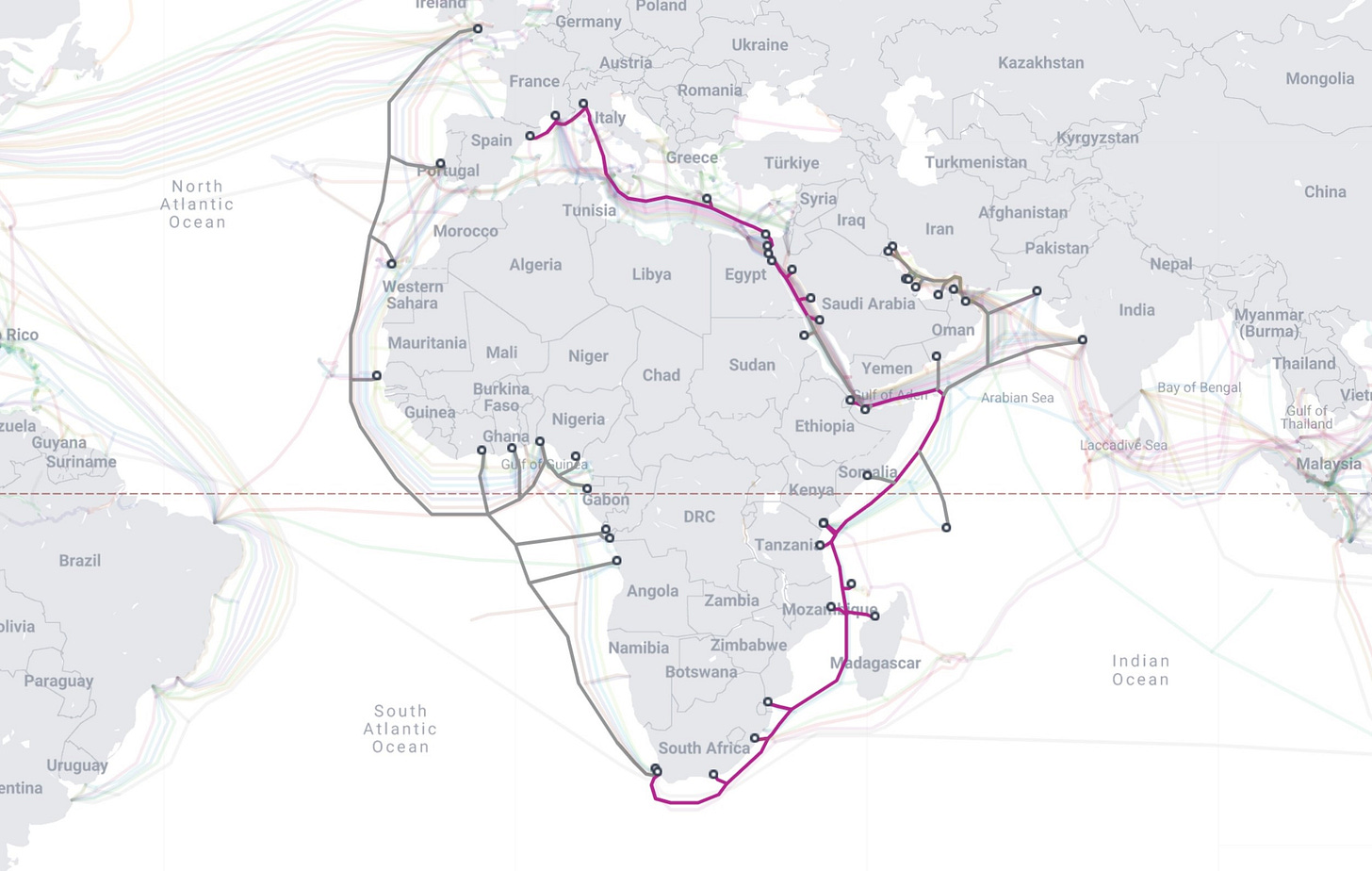
Despite this progress, Africa remains underserved by global internet infrastructure. Africa, with over 17% of the world's population, is still connected by a fraction of the world's subsea cables compared to continents like North America and Europe. This "connectivity gap" impacts everything from economic growth and educational access to the development of local digital ecosystems.
In theory, this encourages design innovation, some of which is already being fulfilled by early efforts. Most of the world’s innovative subsea cable projects are connected to Africa.
Africa is Predator’s largest market
Recorded Future’s Insikt Group’s latest research is a sprawling paper on Predator spyware’s continued presence and activity, especially in Africa. It is the first report that will link the use of Predator with Mozambique, but it also mentions other African countries, including the DRC, Angola, Egypt, and Botswana. According to Recorded Future, over half of Predator current operators are African.
CybAfrique OGs remember that one of our earliest newsletters was about Predator being exported to Sudan’s RSF in the earliest days of the Sudan conflict. As reported by Haaretz, the exchange between Predator’s creators, Tal Dilian and Sara Aleksandra Fayssal Hamou, a corporate off-shoring specialist, had been facilitated through Cyprus. When we at CybAfrique think about how persistent Predator has remained active despite significant public backlash, the first thing that pops up is the group’s understanding of international bureaucracy and how to maneuver it.
ICYMI: Spyware in Sudan
Just like its Sudan deal passed through a Cypriot proxy, most of the group’s interactions with anyone pass through proxies, sometimes multiple layers of corporate and infrastructural proxies. Along with personal and business proxies, researchers at Recorded Future uncovered four infrastructural layers geared mostly at anonymizing and deleting traces of the group’s activities.
Unlike its Pegasus counterpart, Predator has almost thrived in the wake of public scandals. The original creators of the spyware “transferred” ownership to another body, Intellexxa, a coalition of surveillance companies.
Africa remains a prime market for Israeli spyware and surveillance products, including Pegasus, Predator, and RLC, which was caught up in a broader corruption case in Ghana earlier this year.
ICYMI: Ghana spyware scandal
Authorities in Nigeria, Kenya, Ghana, Morocco, Malawi, Rwanda, and Zambia are among the biggest surveillance spenders, throwing in an estimated $1 billion on digital surveillance contracts with companies across the US, UK, China, Germany, Italy, Turkey, and Israel. In the past few years, China has risen to prominence, displacing mostly Western players, but Israel has remained a top actor, especially when it comes to spyware.
China’s rise has been on the infrastructure front, which is significantly cheaper and politically side-stepping than any other player. Huawei, owned by China, is a major distributor of surveillance tech and data centers in Africa. Its technicians have also been accused of helping the governments of Uganda and Zambia spy on political opponents. In 2019, the Ugandan Police Force installed a $126 million facial recognition infrastructure from Huawei across the country. The company has similar projects in development across other countries, including Kenya, Botswana, Mauritius, and Zambia. In 2022, Huawei was given the contract to build a new satellite-based electronic monitoring system along sections of Nigeria’s 5,000-kilometre border to monitor the flow of illegal immigrants and to provide early detection of security threats.
FEATURES
Sophisticated Chinese cybercrime networks are rapidly expanding their operations into African nations like Nigeria, Angola, and Namibia, creating a significant and growing threat to the continent. Driven out of Asia by law enforcement crackdowns, these syndicates establish footholds in Africa to perpetrate global fraud schemes, such as the "pig butchering" cryptocurrency scam, where victims are lured into fake investments and then have their funds stolen. Read more.
There’s an escalation in cyber threats faced by militaries, particularly in Africa, where cyberattacks are rampant and often manifest as disinformation campaigns designed to destabilize nations. This article emphasizes that these threats are not merely technological but are also made to exploit human vulnerabilities. Read more.
HEADLINES
Chinese Cybercrime Networks Spread ‘Like A Cancer’ Into Africa
ngCERT alerts Nigerians to new Android malware targeting WhatsApp and banking apps
Police bust syndicate ‘hijacking’ WhatsApp of prominent Nigerians and defrauding their contacts
Starlink Goes Live in the Democratic Republic of Congo, Expanding Its African Footprint
Nigeria jails 9 Chinese nationals for being part of an international cyberfraud syndicate
Kenya’s Crypto Tax Gamble Threatens Africa’s Digital and Fintech Future
Botswana's Natural Gas-Powered Data Centre To Open In September
Kenya to track crypto transactions in real-time with new tax system
Tunisia: Companies urged to adopt electronic invoicing by July
ACROSS THE WORLD
WhatsApp moves to join Apple’s encryption fight with the U.K. government
AI-driven ransomware tops 2025 cyber threats in META, says Kaspersky
Iran-linked hackers target Kurdish and Iraqi officials in long-running cyberespionage campaign